Microsoft published a support article about the recently disclosed CVE-2022-40982 vulnerability, commonly referred to as Downfall, that affects Windows devices.
The vulnerability was disclosed earlier this month. It affects several Intel processor versions and all supported versions of Windows 10, Windows 11 and Windows Server versions 2019 and 2022.
Microsoft provides guidance about the security issue in the support document KB5029778. There, the company explains how system administrators may install protections against potential exploits and how to disable the protections.
Successful exploitation of the vulnerability could "be used to infer data from affected CPUs across security boundaries such as user-kernel, processes, virtual machines (VMs), and trusted execution environments".
Administrators need to install the Intel Platform Update 23.3 microcode update to mitigate the vulnerability. The update is usually supplied by the original equipment manufacturer and Microsoft recommends to contact the manufacturer for information on obtaining and installing the update. A list of companies and links to driver and software download websites are available on the Intel website.
Intel's latest products are not affected by the vulnerability, including Alder Lake, Raptor Lake and Sapphire Rapids.
The mitigation is enabled by default on systems on which the update is installed. While disabling the mitigation is not recommended in most cases, it is a possibility. Microsoft explains that the mitigation can be disabled if the vulnerability is not part of the threat model. Previous mitigations could impact the performance of the system. While it is too early to tell if the new protection will also impact performance, it is a possibility.
Disabling is only an option if the following Windows updates have been installed:
- Windows 10 and Windows 11: if the August 22, 2023 updates or newer updates have been installed.
- Windows Server: if the September 12, 2023 updates or newer updates have been installed.
Windows administrators may run the following command from an elevated command prompt window to disable the mitigation on Windows client and server devices:
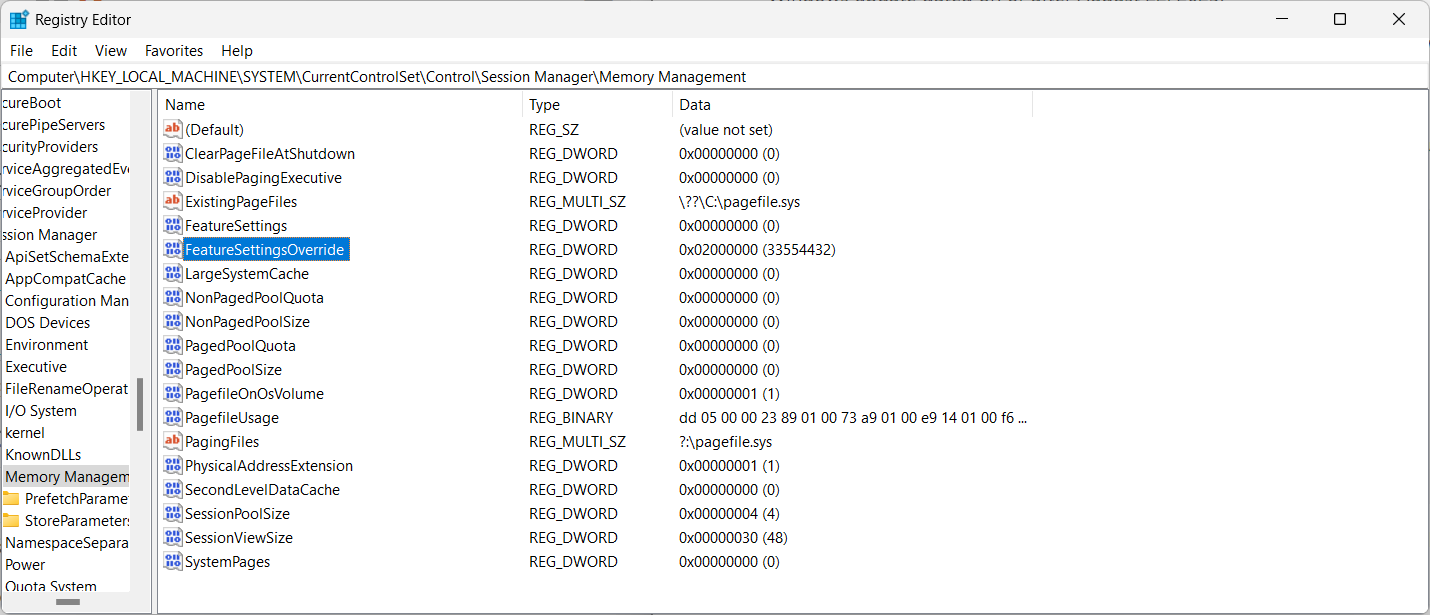
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 33554432 /f
Administrators who prefer to set the appropriate flag manually may do so as well.
- Open the Registry Editor on the Windows machine, e.g., by opening Start, typing regedit and select Registry Editor.
- Confirm the UAC prompt that is displayed.
- Go to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management. If a key does not exist, right-click on the previous key, select New > Key, and name it accordingly to create the path.
- Right-click on Memory Management and select New > Dword (32-bit) Value.
- Name the Dword FeatureSettingsOverride.
- Double-click on the newly created Dword and set its value to 2000000 as Hex.
- Restart the system.
The mitigation is disabled and the system is no longer protected against attacks targeting the vulnerability. This disabling can be undone at any time by deleting the Dword in the Registry.
Thank you for being a Ghacks reader. The post Microsoft publishes mitigation instructions for Downfall vulnerability in Windows appeared first on gHacks Technology News.

0 Commentaires