KeePass Password Safe is an open source local password manager for Windows. It is a well designed application that supports plugins and there are numerous forks available for other platforms.
The Federal Cyber Emergency Team of Belgium, cert.be, released a warning regarding KeePass. According to the warning, attackers with write access to the KeePass configuration file may modify it with triggers to export the entire password database in cleartext without user confirmation.
Triggers automate workflows in KeePass 2.x. They are run automatically when all trigger conditions are fulfilled. Triggers may be used for a variety of tasks, including exporting the active database to a file or URL. The official help file has a section on Triggers in KeePass.
The vulnerability described requires write access to the KeePass configuration file. An attacker has to add a trigger to the file that executes when a password database file is open to export the data silently in the background. Passwords are saved in clear text to a file and the attacker would need to obtain that file later on to gain access to all stored passwords.
Vulnerability is disputed
KeePass disputes the vulnerability. It is described on the official security issues page of the KeePass website.
The main argument leveled against the vulnerability is that if an attacker has write access to the system, that system is compromised and not secure anymore. With write access, an attacker may "perform much more powerful attacks than modifying the configuration file".
The attacker could simply replace the KeePass executable with a malicious one, add malicious programs to the system's autostart, modify configuration files for other apps or change Registry information.
KeePass argues that the only way to prevent password theft is to keep the computing environment secure. Systems need to be protected with anti-virus software, a firewall, and users should not run actions on the systems, such as opening unknown e-mail attachments, to keep it secure.
Mitigation options
KeePass won't get confirmation options implemented when certain triggers are executed. A user of the software suggested the feature, but it has been closed.
Dominik Reichl, the developer of the password manager, argues that users can already block triggers through the use of an enforced configuration file. The special configuration file has priority over the regular configuration file of the KeePass password manager.
The use of the enforced configuration file does not address the underlying issue. Even if write access is disabled to KeePass files and folders, to make sure that an attacker could not modify the enforced configuration file without elevated rights, an attacker might still be able to launch a different instance of KeePast to load the database. Enforced configuration files apply only to Keepass executable files in the same directory.
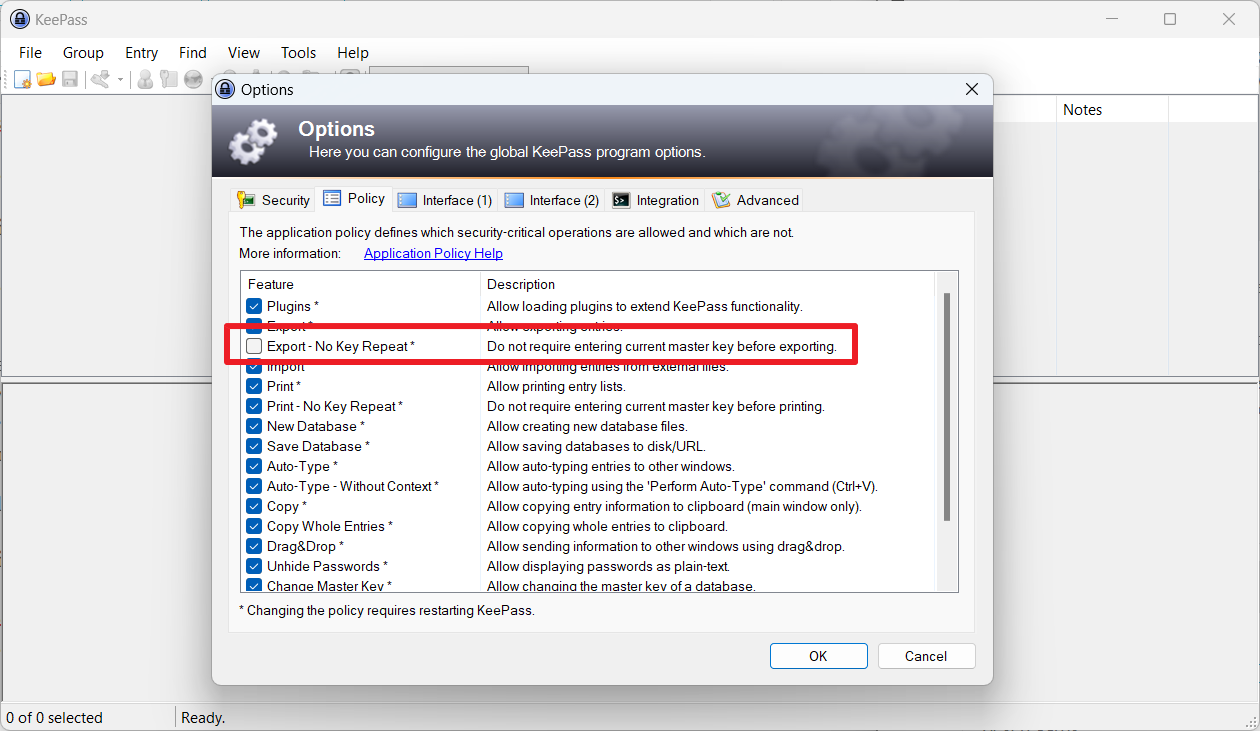
KeePass users find an option in the settings to require a master key when exporting. The setting is found under Tools > Options > Policy > Do not require entering current master key before exporting. Users need to uncheck the box to disable exporting without requiring a master key.
Attackers may turn this off, however, if they have write access to the system. KeePass users have some options at their disposal.
Option 1: Switching to KeePass 1.x
KeePass 1.x is a limited version of the password manager that does not support triggers. KeePass 1.x is still in development.
It needs to be noted that KeePass 1.x lacks support for several features other than triggers. The password manager version does not support one-time passwords, smart cards, certificates, entering the master password on secure desktop, FIPS mode, custom string fields, the entry history, or recycle bin.
A full list of differences is available here.
Option 2: Switching to KeePassXC or another fork
KeePassXC does not support triggers. It loads KeePass database files and may be used instead of KeePass. Other KeePass forks may also be used.
Closing Words
Keeping a computer system secure is of paramount importance. Attackers who gain access to a system have lots of options at their disposal regarding data theft and other malicious activities. Still, triggers make the exporting of entire password databases simple.
Now You: which password manager do you use? (via Günter Born)
Thank you for being a Ghacks reader. The post KeePass Password Manager vulnerability: what you need to know appeared first on gHacks Technology News.
0 Commentaires