When it comes to ransomware attacks, some data is more precious to ransomware groups as others. A new research study by Rapid7, Pain Points: Ransomware Data Disclosure Trends, provides insight on the data that ransomware groups value and how they use data to apply pressure.
Double extortion attacks have increased in recent years. Traditional ransomware attacks encrypt data on attacked systems to extort money from companies and individuals. The rise of countermeasures, including the use of backups, have reduced the effectiveness of traditional ransomware attacks.
If data backups are available, companies could use these to restore the data without having to pay ransom. Without additional leverage, ransomware groups would be left empty handed after the attack.
Double extortion attacks combine the encryption stage with another stage, which happens before data is encrypted. Groups analyze files and documents on the attacked network to steal data. Data is still held hostage, as it is encrypted in the second stage, but the stolen data may be used as leverage in ransomware negotiations. Ransomware groups may threaten to release the data to the public, or sell it to interested parties. If negotiations fail, data may be sold on the dark web.
Ransomware studies are released frequently. We have covered two here on Ghacks in the past two months alone. The first, confirms that ransomware attacks and ransom payments are increasing. The second, that the ransom payment is marginal when compared to the overall costs of ransomware attacks.
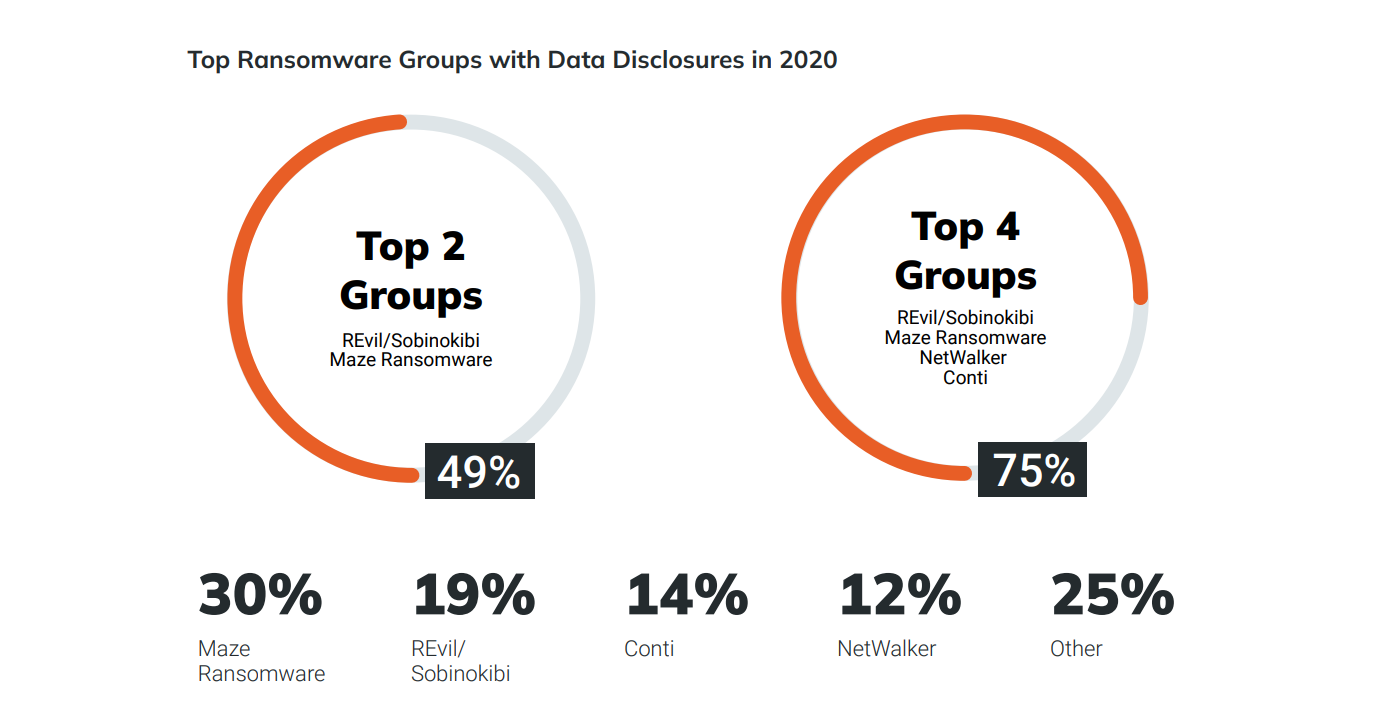
Ransomware Data Disclosure
Rapid7 analyzed 161 data disclosures between April 2020 and February 2022. Many ransomware attacks happen over the course of days, weeks or even months. The time span gives attackers time to collect and exfiltrate data from compromised networks before running encryption tasks.
Some data is more valuable to ransomware groups than others. Data that may be used as leverage, for instance patient files, financial documents, or intellectual property files, are more valuable on average than other types of data that attackers may discover during attacks.
The extracted data is used in various ways by ransomware groups. Besides obvious uses to gain even deeper access to the network of the organization, exfiltrated data may also be used as leverage, or sold on dark web markets if ransomware negotiations fail.
The extra time that attackers spend on a network gives organizations an opportunity to detect the compromise before data is fully encrypted.
Ransomware data disclosures happen in two stages:
- Stage 1: A sample of the stolen data is presented to the organization; this is done to improve credibility and as leverage, as further data disclosures may prove damaging to the organization. The data is provided to the organization only usually, but it may also be published publicly on the Internet.
- Stage 2: Data is sold or published, if negotiations with the victim were fruitless.
Rapid7 notes in the analysis that data disclosures are indicators of general ransomware trends. Company researchers were able to determine the following based on the analysis of the 161 data disclosures:
- Most common types of data attackers disclosed
- How data disclosures differ between industries and threat actor groups.
- Current ransomware market share among threat actors.
Data Sets in Ransomware Data Disclosures
Not all data is of equal importance to organizations, and data disclosures may differ widely between sectors. Most thought after were customer & patient data in financial services attacks, finance and accounting information in healthcare and pharmaceutical attacks, and employee PII & HR in Financial services.
Notably, intellectual property data was used in 43% of pharmaceutical disclosures. For all industries, finance & accounting information was used the most, followed by customer & patient data, and employee PII & HR data.
Customer data disclosures dominated the Financial Services sector, followed by employee PII & HR data, and internal finance and accounting documents. The focus on customer data suggests that customer data is often more valuable to ransomware groups than other types of data. Rapid7 suggests that the threat of releasing customer data is often powerful, as it could affect the organization's public perception.
Internal finance and accounting files were disclosed in healthcare and pharmaceutical the most, and not in financial sector disclosures. Customer and patient data was disclosed in more than 50% of all cases, but not nearly as much as in financial services.
The high frequency with which Customer & Patient Data appears in these disclosures suggest attackers aim to exert greater pressure on victims with: a) the more severe legal and regulatory consequences of patient data breaches for hospitals and other healthcare providers and; b) the greater utility of the more detailed and granular patient data sets to criminals for identity theft and other forms of fraud.
Disclosures from the pharmaceutical sector had a high frequency of intellectual property files. Pharmaceutical companies "depend heavily on large intellectual property investments", which makes these data discloses valuable to threat actors. Intellectual property disclosures were included in just 12% of disclosures of all samples.
Threat Actor Group Trends
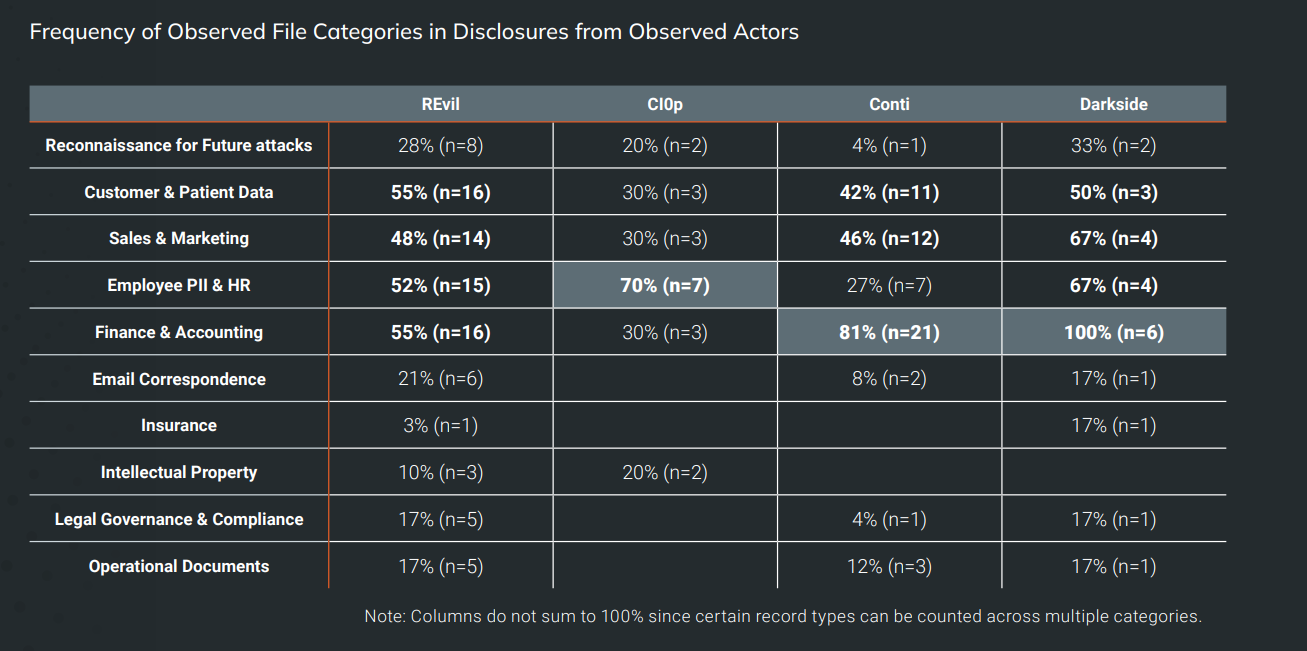
Threat Actor Groups use different strategies when it comes to double extortion attacks. Some of the differences may be explained by the data that the attackers discovered during attacks. If a certain type of data is not found or can't be exfiltrated, other data may have been used instead as leverage.
The four main groups of the analysis used different data types in disclosures. Finance & account data was disclosed 100% by the group Darkside, but only 30% of the time by CI0p. Similarly, Darkside disclosed sales & marketing, and employee Pii & HR data 67% of the time, while other groups only 27% or 30% of the time.
Recommendations and suggestions by Rapid7
More and more organizations use backups to counter traditional ransomware attacks. Backups help, but they are not 100% effective on their own when it comes to double extortion attacks. To counter double distortion attacks, Rapdi7 suggests that organizations use file encryption, segment company networks, and render "any files unreadable to unauthorized eyes".
The report may assist organizations in determining high priority assets to better protect these against potential ransomware attacks.
Organizations, finally, may also use the findings of the report in preparations to "anticipate what types of
files are most likely to appear".
Now You: how do you protect your systems against ransomware attacks? (via Rapdi7)
Thank you for being a Ghacks reader. The post Rapid7 research reveals which data ransomware groups seek and use for leverage appeared first on gHacks Technology News.
0 Commentaires