Scammers are targeting users of cloud-based password managers, including Bitwarden, with phishing attacks. And the mode of attack was malicious ads.
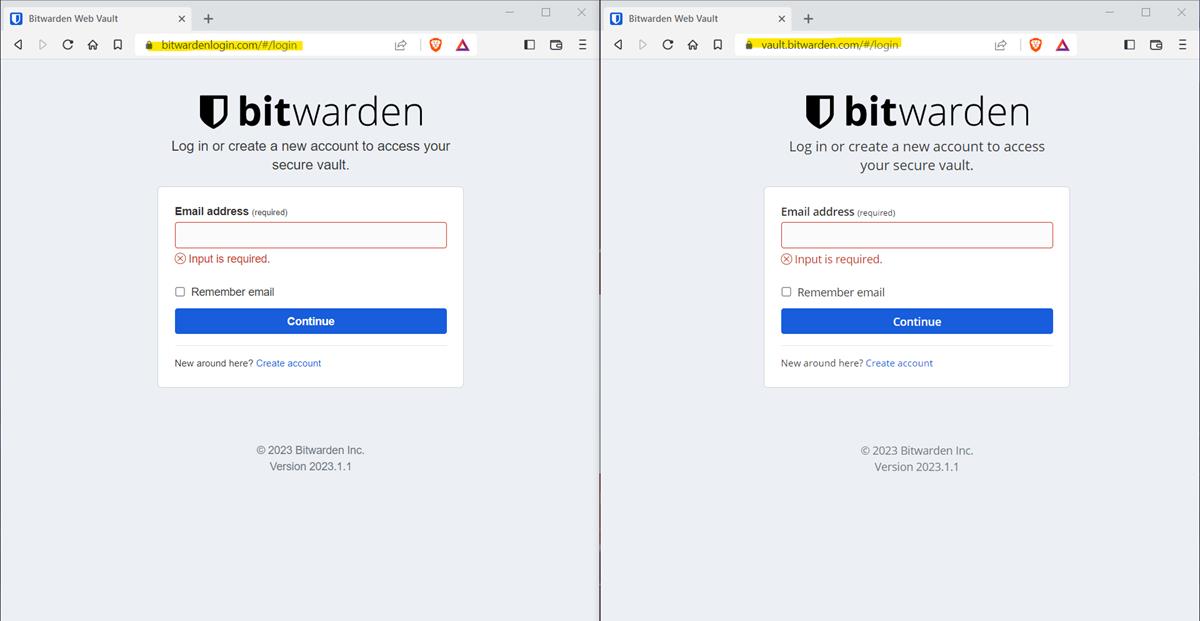
Users have reported that they have seen fake advertisements for Bitwarden on Google, the links in the ads were however not related to the password manager's websites. The above image is from a reddit user who posted it a couple of days ago. This particular website closely resembles Bitwarden's login page. Now what would happen if a user entered their username and the master password that unlocks their vault, and the scammers get hold of that information. The attackers could try using the obtained credentials and login to the accounts on Bitwarden's servers, to steal the contents of the password vault. But these phishing campaigns are actually a little more sophisticated, hackers often steal authentication tokens too.
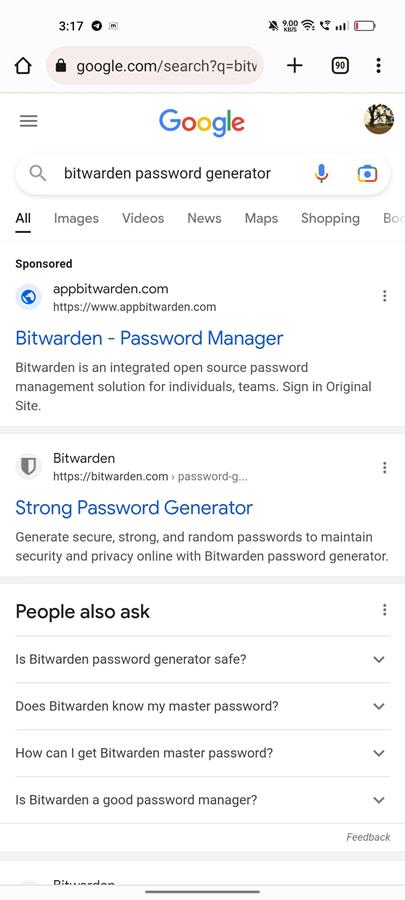
Here's a look at the malicious ad (h/t reddit), shockingly these malicious pages were placed at the top of the search results, above the legitimate URL itself. Do you see what happens when you don't use an ad blocker? uBlock Origin is my recommendation, feel free to check AdGuard or something else that fits your bill, just make sure it's a reputable extension/app, do your homework.
Another Bitwarden user created a thread on the company's support portal, to alert others about the website that was trying to impersonate the official website's login page. It is quite alarmingly similar, isn't it? Everything from the fonts, icons, and other elements on the phishing site looks identical to the original login page.
BleepingComputer says it ran some tests by entering some credentials on the site, but once it accepted them, the malicious web page redirected users to the official Bitwarden site. The writer states that they were unable to test the phishing page with real login information, or authentication tokens, as the site was taken down by then.
I suppose users might still be safe if they have 2-factor authentication enabled for their accounts, but still, this is pretty scary. It emphasizes the need to check the URLs with a close eye. If you want to access your web vault, you can use the Bitwarden Desktop app's Help > Go to vault option to access the correct web page, which is https://ift.tt/79Oqhkd. You may want to save that to your browser's bookmarks. Users of the Bitwarden browser extension for Firefox and Chrome can access the page by clicking the add-on's icon > Settings > Bitwarden web vault. Make sure you use a strong and unique master password, enable two-factor authentication (2-step verification) on your account, and pay attention to the web page that you are on before providing your username and password to it.
Malvertising and phishing attacks could happen to any cloud-based password manager or any cloud service for that matter, Bitwarden users aren't the only ones who have been targeted by these, MalwareHunter reports that a similar phishing campaign was used to lure and trick 1Password users, also using malicious ads on Google. This is a serious problem. Recently, Norton Password Manager users were victims of a password stuffing attack. The biggest password manager breach in recent times (biggest in history?), was of course the LastPass incident, which resulted in hackers gaining access to cloud servers that contained the password vaults of the company's users.
I'm never going to stop recommending KeePass to people who are afraid of cloud services. KeePass is free, open-source, works offline, supports physical security tokens, has excellent forks and ports for iOS, Android, Linux, macOS and Windows. What's not to like about it? Even if you do use cloud-based services, you should consider exporting a copy of your password vault and import it to KeePass. This way, even if the cloud-app suffers an outage, you won't be locked out of your accounts.
Thank you for being a Ghacks reader. The post Bitwarden Password Manager users are being targeted by phishing ads on Google appeared first on gHacks Technology News.
0 Commentaires