Twilio, the company which owns the popular 2-factor authentication service Authy, has revealed that it has suffered a data breach. An announcement published on its website states that some of its employees fell victim to a phishing attack.
Twilio data breach
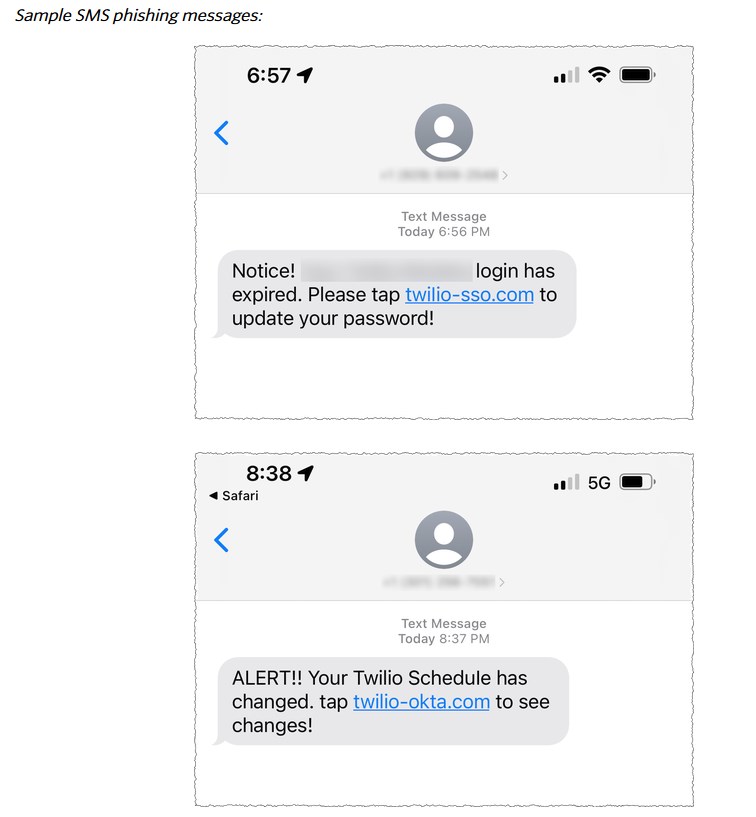
According to the report, hackers sent some text messages to current and former employees of the company. The message which originated in the U.S., was spoofed as being sent from Twilio's IT department, asked the users to update their passwords. A link, which accompanied the texts, directed the users to URLs controlled by hackers, who then stole the credentials to gain access to some of the company's internal systems.
The concerning part is that the attackers were able to access certain customer data. Twilio is investigating the attack, and will notify customers who were affected by the data breach. The company has already revoked access to the compromised accounts. It says that it worked with US carriers to shut down the threats, and has taken down the accounts belonging to the attackers on hosting providers that were used for the breach.
The transparency related to the data breach might be appreciated by users, but the company has not clarified what customer data was accessed. Twilio owns several products and services, Authy is just one of those, and is probably the most popular one of the lot. The attack will no doubt raise some eyebrows about the safety of Authy.
Are Authy users safe?
There is no official word whether user data from Authy has been stolen. I have seen a few reports on social media where users are panicking. But, I think it is safe to say that Authy users shouldn't be worried. Why is that?
1. Authy's login system
2. End-to-end encryption
Authy does not have a traditional login system, i.e. a username and a password. Instead, the service uses your phone number as your login ID. Let's say a hacker somehow knows your phone number, they can't associate it with your account's data. Since the TOTP service does not employ a password system, your credentials are not saved on the cloud, i.e. there is no password to be leaked. Authy uses a protection PIN (pass code) which serves as the encryption key to encrypt your data (2FA account tokens) on your device before it is uploaded to the cloud, this is known as end-to-end encryption. The only person who has access to this encryption key, is the user, without this key the data cannot be accessed by anyone, even Authy itself can't get the TOTP codes. Similarly, when you download Authy on a new device, you need to input the pass code to decrypt the data, before using the app for 2FA codes.
This end-to-end encryption is essentially similar to how cloud-based password managers work, for example, Bitwarden. Even if a hacker has managed to breach Authy, your data should theoretically be safe because the contents are encrypted. That's the whole point of encryption.
This is not an official explanation from the company, it's just based on my understanding of how end-to-end encryption works. Of course, it all depends on the proper implementation of the encryption system.
Some of my friends rely on Authy across platforms (iOS, Android), but I moved away from Authy a few years ago, to Aegis because I prefer offline and open source apps. I used this guide for importing the tokens.
Do you use Authy?
Thank you for being a Ghacks reader. The post Twilio, the company that owns Authy, suffered a data breach appeared first on gHacks Technology News.
0 Commentaires