Google released a new version of the company's Google Chrome browser on August 16, 2022. The new stable version is a security update for the browser that addresses 11 security issues.
It fixes a critical security issue in the browser and a high security issue that is exploited in the wild.
The update is also available for the Extended Stable channel, a longer-term support release version of Chrome for businesses and Enterprise users.
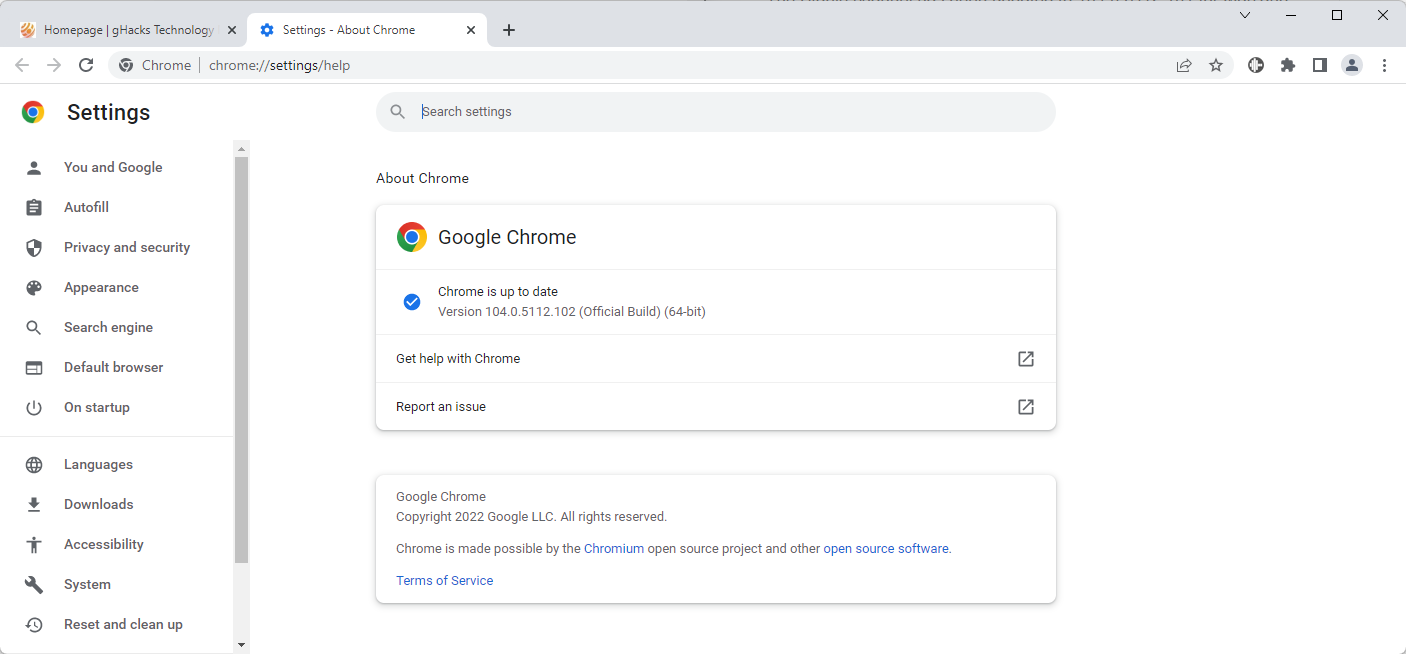
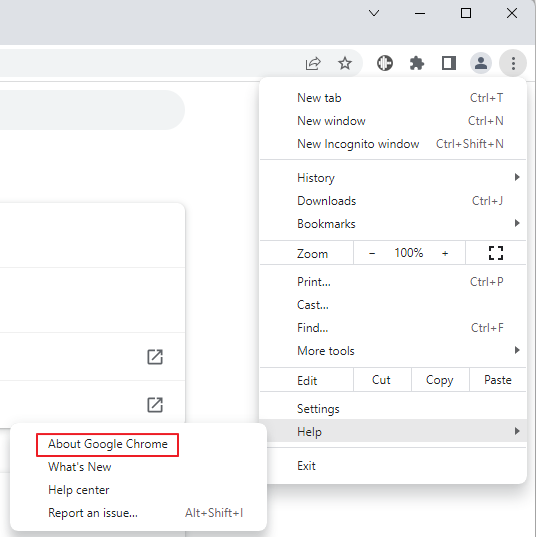
The update is available already, but it is distributed in waves. Chrome users who want to update to the new version immediately need to select Menu > Help > About Google Chrome, or load chrome://settings/help directly in the browser.
Chrome displays the current version of the browser and performs a check for updates at the same time. The new update is downloaded and installed automatically then. A restart is required to complete the update.
Chrome 104 security update
Google released the first version of Chrome 104 in early August. The release fixed 27 security vulnerabilities in the browser.
The stable channel is updated to 104.0.5112.101 for Mac and Linux, and 104.0.5112.102/101 for Windows when the update is installed. Extended stable channel installations are updated to updated to 104.0.5112.101 for Mac and 104.0.5112.102 for Windows.
The release announcement lists all security issues that have been reported to Google by external researchers. Google does not list security issues that it discovered internally.
- [$NA][1349322] Critical CVE-2022-2852: Use after free in FedCM. Reported by Sergei Glazunov of Google Project Zero on 2022-08-02
- [$7000][1337538] High CVE-2022-2854: Use after free in SwiftShader. Reported by Cassidy Kim of Amber Security Lab, OPPO Mobile Telecommunications Corp. Ltd. on 2022-06-18
- [$7000][1345042] High CVE-2022-2855: Use after free in ANGLE. Reported by Cassidy Kim of Amber Security Lab, OPPO Mobile Telecommunications Corp. Ltd. on 2022-07-16
- [$5000][1338135] High CVE-2022-2857: Use after free in Blink. Reported by Anonymous on 2022-06-21
- [$5000][1341918] High CVE-2022-2858: Use after free in Sign-In Flow. Reported by raven at KunLun lab on 2022-07-05
- [$NA][1350097] High CVE-2022-2853: Heap buffer overflow in Downloads. Reported by Sergei Glazunov of Google Project Zero on 2022-08-04
- [$NA][1345630] High CVE-2022-2856: Insufficient validation of untrusted input in Intents. Reported by Ashley Shen and Christian Resell of Google Threat Analysis Group on 2022-07-19
- [$3000][1338412] Medium CVE-2022-2859: Use after free in Chrome OS Shell. Reported by Nan Wang(@eternalsakura13) and Guang Gong of 360 Alpha Lab on 2022-06-22
- [$2000][1345193] Medium CVE-2022-2860: Insufficient policy enforcement in Cookies. Reported by Axel Chong on 2022-07-18
- [$TBD][1346236] Medium CVE-2022-2861: Inappropriate implementation in Extensions API. Reported by Rong Jian of VRI on 2022-07-21
The list includes a security issue with a critical severity rating. The remaining security issues have a rating of high or medium. The critical issue was discovered in FedCM, Federated Learning with Client-level Momentum.
Google mentions that the security issue CVE-2022-2856 is exploited in the wild. The issue is rated high and has the description "Insufficient validation of untrusted input in Intents".
Chrome desktop users should consider updating the browser as soon as possible to fix the security issues and protect their data from attacks that target these issues. Expect updates from other Chromium-based browsers in the coming days and weeks.
Now You: do you use Google Chrome?
Thank you for being a Ghacks reader. The post Google Chrome 104: patches critical security issue and a issue that is exploited appeared first on gHacks Technology News.

0 Commentaires