Intel published two security advisories for many of the company's processor generations this week. The vulnerabilities have received a severity rating of high, the second-highest after critical.
Good news is that the two issues require local access to be exploited. Bad news, that BIOS updates are required to address the issues.
Vulnerabilities CVE-2021-0157 and CVE-2021-0158 may allow escalation of privilege if successfully exploited. The vulnerabilities base score is 8.2, high.
Intel describes the issue in the following way:
Insufficient control flow management in the BIOS firmware for some Intel(R) Processors may allow a privileged user to potentially enable escalation of privilege via local access.
The following processor families are affected by the issue according to Intel:
Intel® Xeon Processor E Family
Intel® Xeon Processor E3 v6 Family
Intel® Xeon Processor W Family
3rd Generation Intel Xeon Scalable Processors
11th Generation Intel Core™ Processors
10th Generation Intel Core™ Processors
7th Generation Intel Core™ Processors
Intel Core™ X-series Processors
Intel Celeron Processor N Series
Intel Pentium Silver Processor Series
It seems strange that Intel processor generations 7, 10 and 11 are affected, but generations 8 and 9 are not.
The second vulnerability, CVE-2021-0146, may allow escalation of privilege as well. It too requires physical access for the attack. The base score of the vulnerability is 7.1, which is also high.
Intel provides the following description:
Hardware allows activation of test or debug logic at runtime for some Intel(R) processors which may allow an unauthenticated user to potentially enable escalation of privilege via physical access.
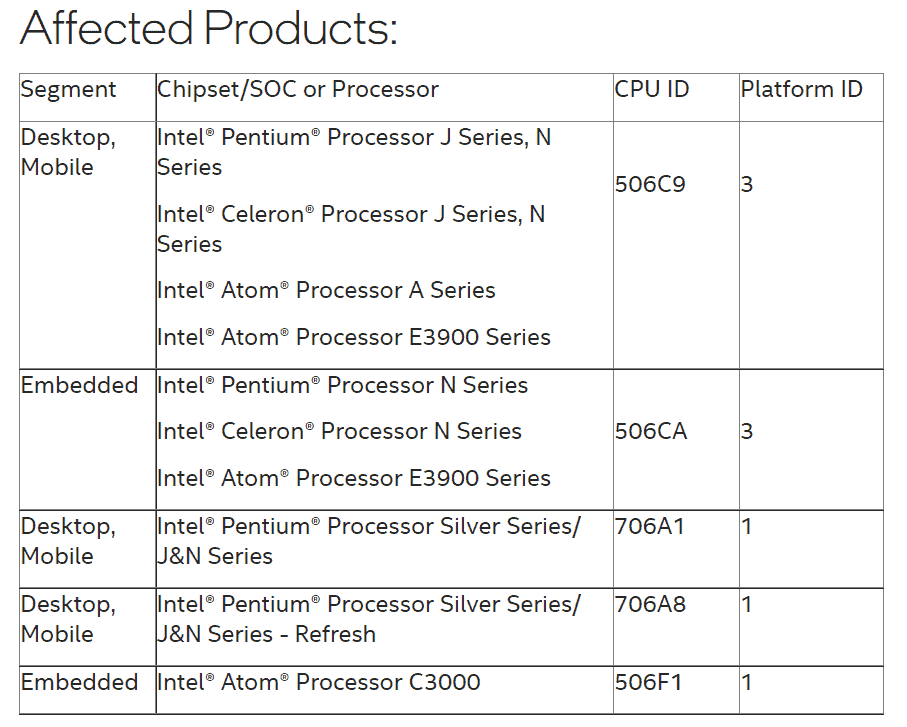
The following Intel products are affected according to the company:
Desktop, Mobile
Intel Pentium Processor J Series, N Series
Intel Celeron Processor J Series, N Series
Intel Atom Processor A Series
Intel Atom Processor E3900 Series
Embedded
Intel Pentium Processor N Series
Intel Celeron Processor N Series
Intel Atom Processor E3900 Series
Desktop, Mobile
Intel Pentium Processor Silver Series/ J&N Series?
Desktop, Mobile
Intel Pentium Processor Silver Series/ J&N Series? - Refresh
Embedded
Intel® Atom® Processor C3000
Resolution
Intel has released updates, but system manufacturers need to provide these to their customers. If the past is anything to go by, it is unlikely that older products will receive BIOS updates that address the issues.
Still, you may want to check the manufacturer's website regularly to find out if an update has been published.
Intel does not reveal additional details on the vulnerabilities. Whether setting a BIOS password is enough to block attacks from being carried out is unclear at this point.
Now You: are you affected by the vulnerabilities? (via Deskmodder)
Thank you for being a Ghacks reader. The post Intel confirms two local security issues that affect many Intel processor generations appeared first on gHacks Technology News.

0 Commentaires